How to Hook Beef on Another Computer in Same Network
Browser Exploitation Framework (BeEF) is a penetration testing, or pen-testing, tool designed to provide constructive client-side attack vectors and to exploit whatsoever potential vulnerabilities in the web browser. BeEF is unique amid pen-testing frameworks considering it does not try to tackle the more secure network interface aspects of a organization. Instead, BeEF clings on to 1 or more than web browsers to utilise every bit a Pavillion for injecting payloads, executing exploit modules, and testing a organisation for vulnerabilities past sticking to browser influenced utilities.
Beef has a very capable, yet straightforward, API that serves every bit the pin upon which its efficiency stands and grows out into an imitation of a full-fledged cyber assail.
This curt tutorial volition take a await at several ways that this flexible and versatile tool can be of use in pen-testing.
Installing the Beefiness Framework
A Linux OS such as Kali Linux, Parrot Os, BlackArch, Backbox, or Cyborg OS is required to install Beef on your local machine.
Although BeEF comes pre-installed in various pen-testing operating systems, it might be possible that it is non installed in your example. To check if whether Beef is installed, await for Beef in your Kali Linux directory. To do then, go to applications>Kali Linux>Organisation Services>beef start.
Alternatively, you tin can fire up Beef from a new terminal emulator past entering the post-obit lawmaking:
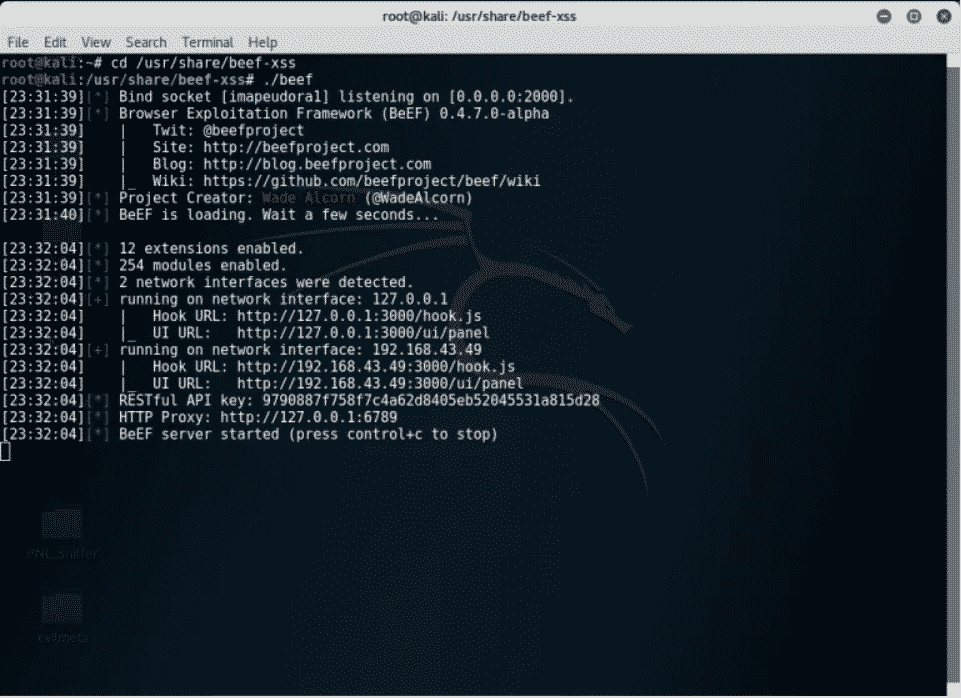
$ cd /usr/share/beefiness-xss
$ cd ./beef
To install BeEF on your Kali Linux machine, open the command interface and type in the following command:
$ sudo apt-get update
$ sudo apt-get install beef-xss
Beefiness should now be installed under /usr/share/beef-xss.
You tin can start using BeEF using the address described previously in this section.
Welcome to BeEF
Now, yous can run into the Beefiness GUI in its full glory. Access the BeEF server by launching your web browser and looking up the localhost (127.0.0.1).
Yous can access the BeEF spider web GUI past typing the post-obit URL in your web browser:
http://localhost:3000/ui/authentication
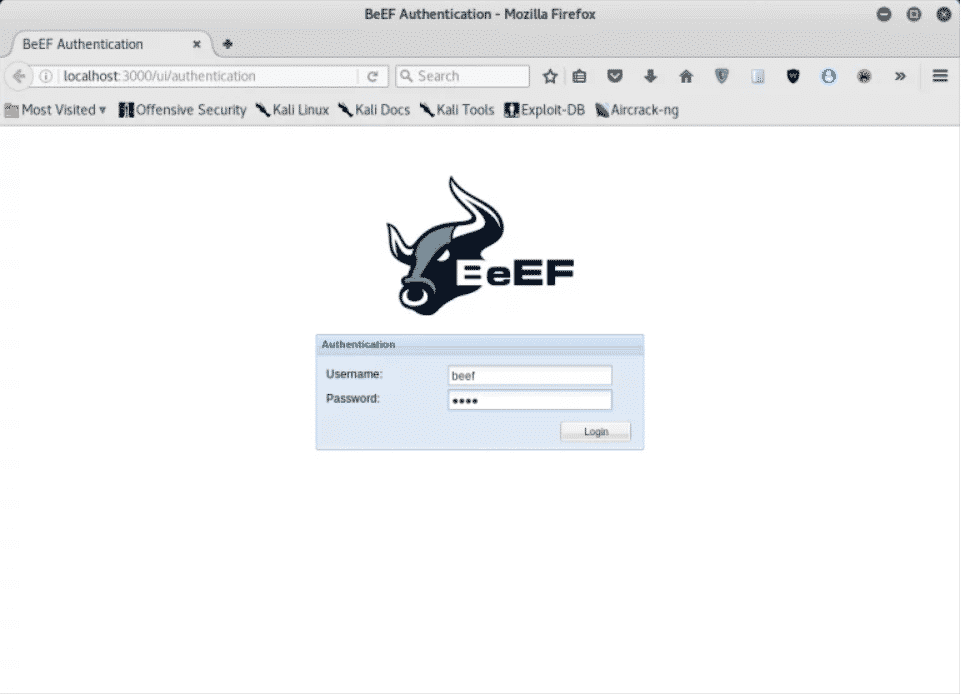
The default user credentials, both the username and password, are "beef:"
$ beef-xss-1
$ Beef Login Web GUI

Now that you have logged into the Beefiness web GUI, keep to the "Hooked Browsers" section. Online Browsers and Offline Browsers. This section shows the victim'southward hooked status.
Using BeEF
This walkthrough will demonstrate how to utilise Beef in your local network using the localhost.
For the connections to be made outside the network, we volition need to open up ports and forward them to the users waiting to connect. In this article, we will stick to our home network. We will discuss port forwarding in future articles.
Hooking a Browser
To get to the core of what Beefiness is about, first, you volition need to sympathise what a Beefiness hook is. It is a JavaScript file, used to latch on to a target's browser to exploit information technology while acting every bit a C&C betwixt it and the attacker. This is what is meant by a "hook" in the context of using BeEF. Once a web browser is hooked by Beefiness, you can go on to inject further payloads and begin with mail service-exploitation.
To discover your local IP address, yous open a new concluding and enter the following:
Follow the steps below to perform the attack:
- To target a spider web browser, y'all will starting time need to identify a webpage that the victim to-be likes to visit often, and then attach a Beef claw to information technology.
- Deliver a javascript payload, preferably past including the javascript hook into the spider web page'southward header. The target browser volition become hooked once they visit this site.
If you take been able to follow these steps without any problems, y'all should be able to come across the hooked IP address and OS platform in the Beef GUI. You lot can find out more than about the compromised organisation past clicking on the hooked browser listed in the window.
Also, in that location are several generic webpage templates they have made available for your use.
http://localhost:3000/demos/butcher/alphabetize.html
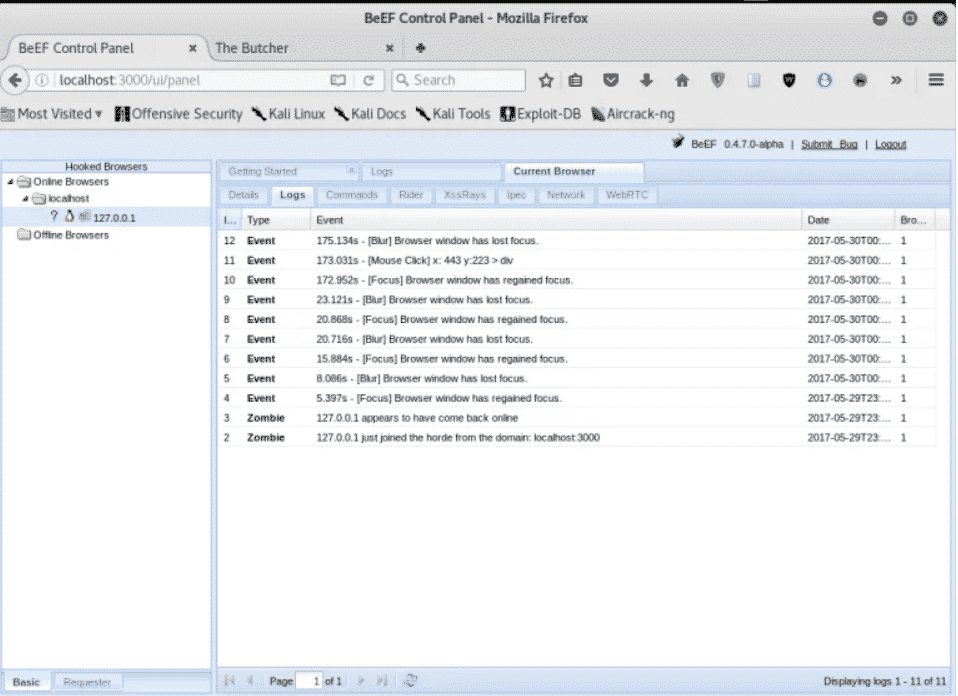
You can glean all sorts of information from here, such as the plugins and extensions that the browser is using, and diverse information about the hardware and software specs of the target.

The Beef framework goes so far as to create complete logs of mouse movements, double-clicks, and other actions performed past the victim.
Here is a list of available modules that can be used to breach a designated arrangement. These modules include keyloggers and spyware, including the ones that use the webcams and microphones of the target browser.
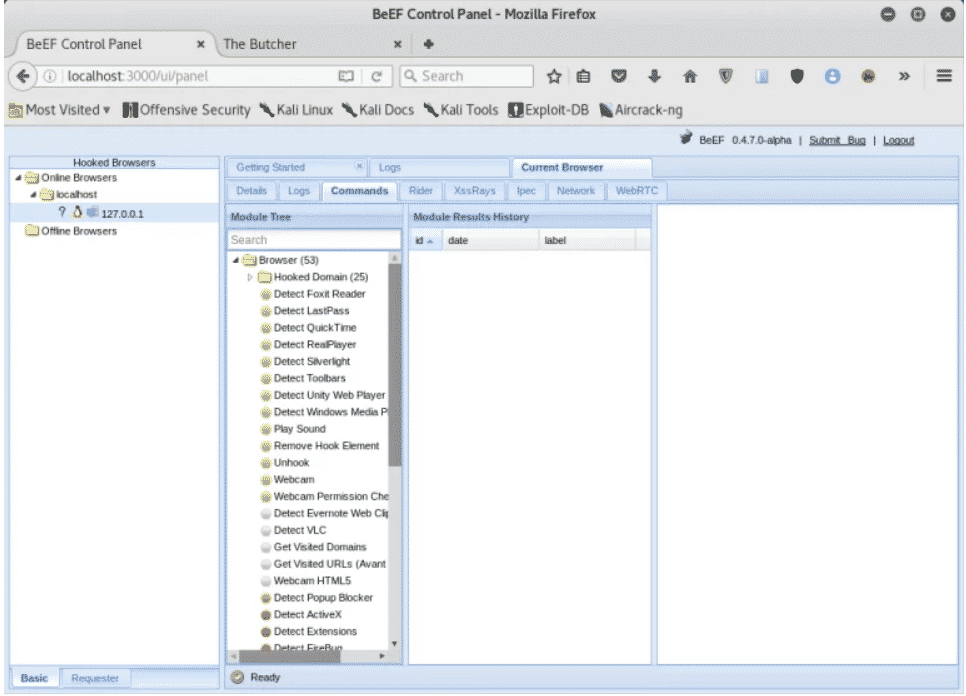
Notation that certain commands accept a colored icon. These icons all have different connotations that yous tin find out by taking the 'getting started' introductory bout, which introduces various aspects of the BeEF interface. Too, discover how each module has a traffic light icon associated with it. These traffic symbols are used to point any of the following:
- The control module works against the target and should exist invisible to the user
- The command module works against the target just may be visible to the user
- The command module has yet to be verified confronting this target
- The command module does not work against this target
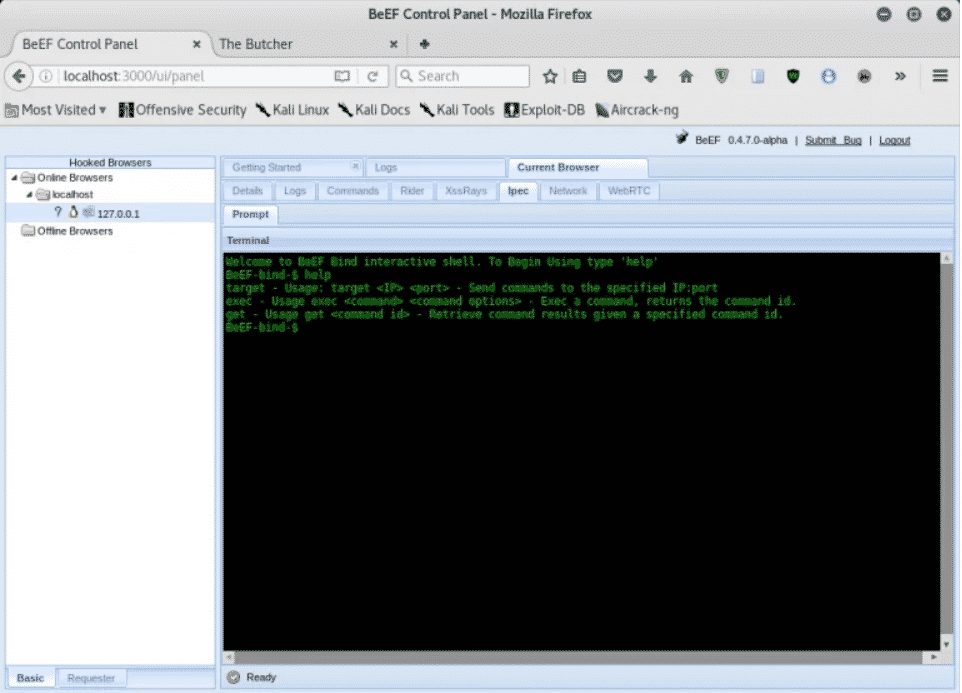
Yous tin also send shell commands to the target arrangement, as shown below:
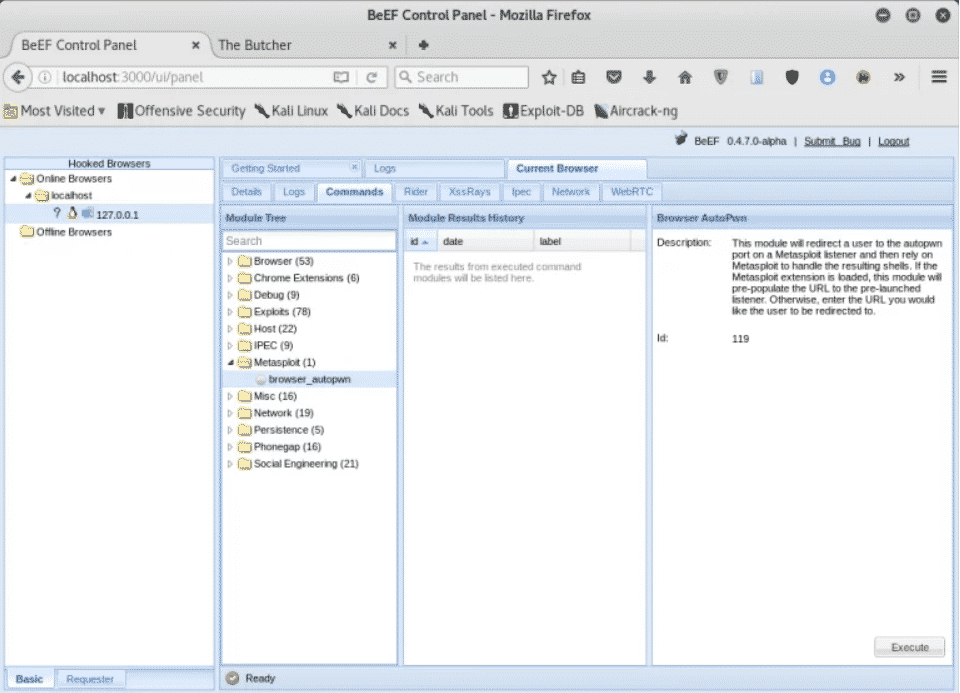
Coupled with Metasploit, BeEF can be used to perform quite varied and intricate organisation exploitation using modules, such equally browser_auto_pwn.
Conclusion
BeEF is an incredibly powerful tool that you can employ to fortify systems confronting cyberattacks. From providing spyware modules to tracking mouse movement on the targeted system, Beefiness can do it all. Information technology is a proficient idea, therefore, to examination your organisation using this security forensics tool.
Hopefully, y'all institute this tutorial useful to become you lot started with this tool with such diverse, useful functionality.
Source: https://linuxhint.com/hacking_beef/
0 Response to "How to Hook Beef on Another Computer in Same Network"
Publicar un comentario